
Bake security into your pipeline without breaking your sprint velocity
Security isn’t someone else’s job anymore
If your dev team owns the infra, runs the CI, and gets paged when deploys break. Congrats, you already own more than just code.
It’s no surprise that security is joining the list. Not as a separate stage, but as part of how you ship.
Security isn’t a signoff anymore. It’s baked in. This shift has a name: SecDevOps.
And it’s not optional. Not when one bad config or stale library can block a release, spark a fire drill, or leave you scrambling to patch a zero-day on a Friday night.
The old model, security as a final gate, doesn’t scale. It slows teams, creates friction, and drops issues in devs’ laps after the code’s out the door.
SecDevOps flips that. Security becomes just another part of the pipeline, like tests, like linting. It runs early, runs often, and runs where devs already work.
When security flows with the code, not against it? You ship cleaner, sleep better, and stop firefighting surprises at the worst time.
What is SecDevOps?
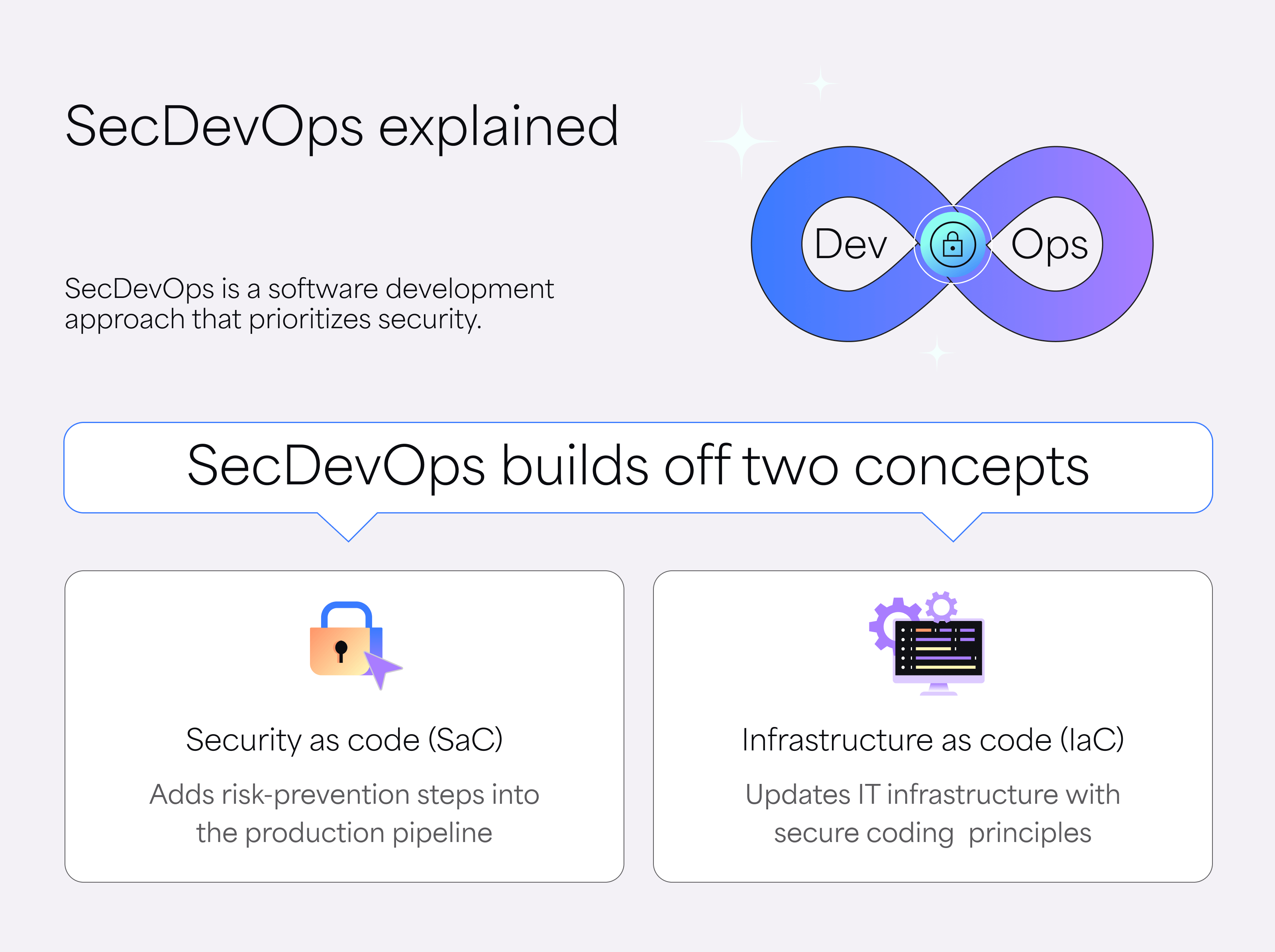
SecDevOps isn’t a new job title. It’s not a buzzword. It’s a shift in how teams ship: security checks baked directly into your delivery pipeline running early, running often, and catching issues before they’re buried.
It’s the idea that secure code is part of “done.”
Instead of waiting on post-deploy security reviews, SecDevOps brings scanning, policy enforcement, and compliance checks into the CI flows devs already use.
- Vuln scans in CI, not after release
- Policy-as-code, not PDF playbooks
- Automated enforcement, not manual gatekeeping
- PR feedback, not email threads weeks later
SecDevOps isn’t about turning developers into security experts. It’s about giving them the right tools and signals, right where they work, so they can ship secure code without extra overhead.
Why SecDevOps beats traditional security reviews
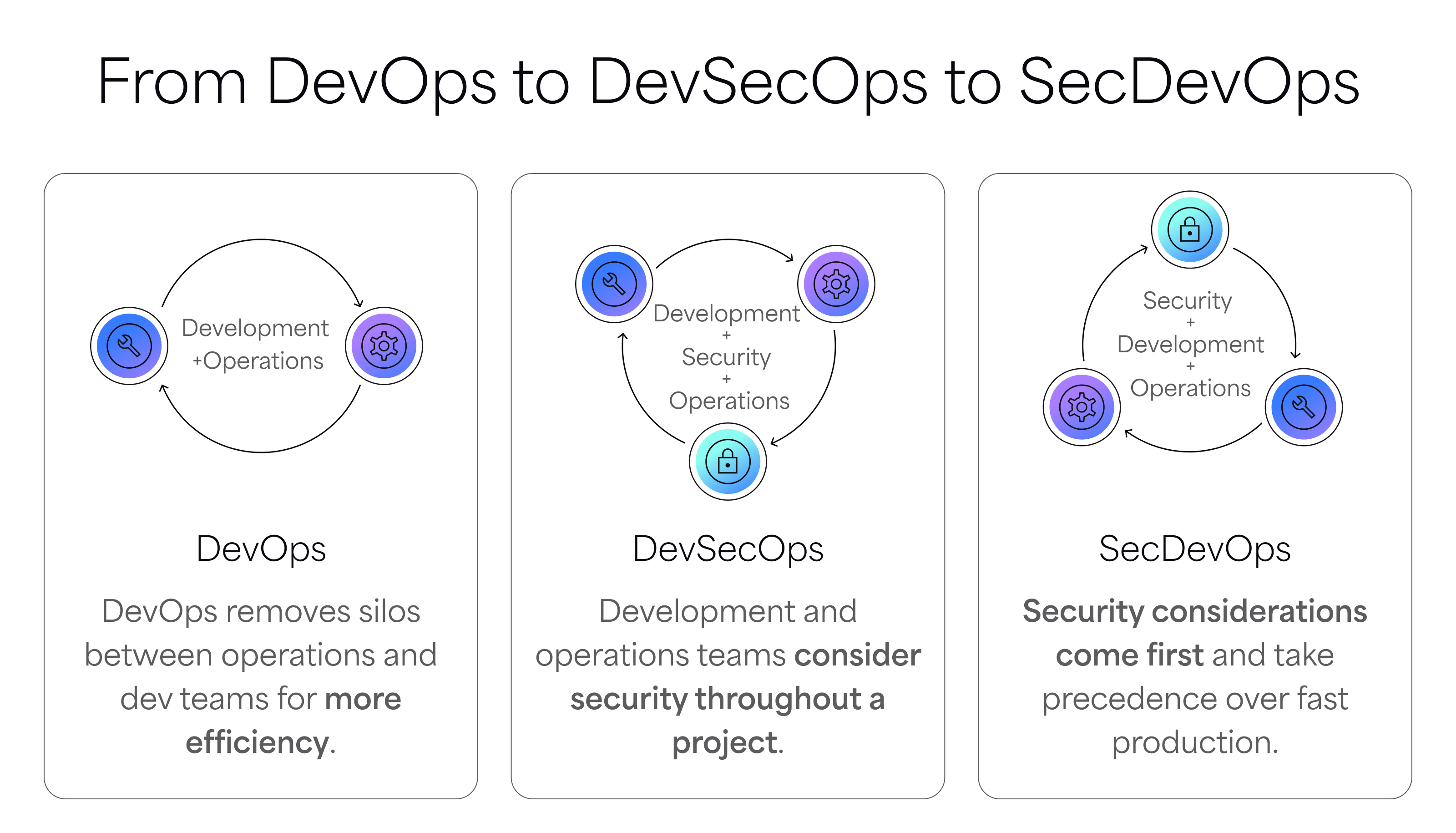
Traditional security reviews weren’t built for CI/CD, they were built for quarterly releases and PowerPoint risk audits. In today’s pipelines, they’re a bottleneck.
The result? Late-stage blockers, rushed hotfixes, or worse. Security steps skipped entirely to meet a ship date.
SecDevOps flips that model. It shifts security left, into the dev flow, where feedback is fast, relevant, and fixable.
Here’s how the shift plays out in real pipelines:
Traditional Security Reviews | SecDevOps Approach |
|---|---|
| Manual reviews after code merges | Automated checks in every PR |
| PDF policies and tribal knowledge | Policy-as-code, enforced in CI |
| Surprise blockers at release | Early, contextual feedback in dev |
| Security as gatekeeper | Security signals in the pipeline |
You’re not cutting corners, you’re shifting the guardrails upstream.
With SecDevOps, issues get caught when they’re easy to fix. Releases land clean. No more wondering if the security team will swoop in with a blocker, you already know, because it’s baked into the pipeline.
How to implement SecDevOps in your team
You don’t need to rebuild your pipeline. You just need to wire security into the one you’ve already got. Think of it as a rewire — not a rewrite.
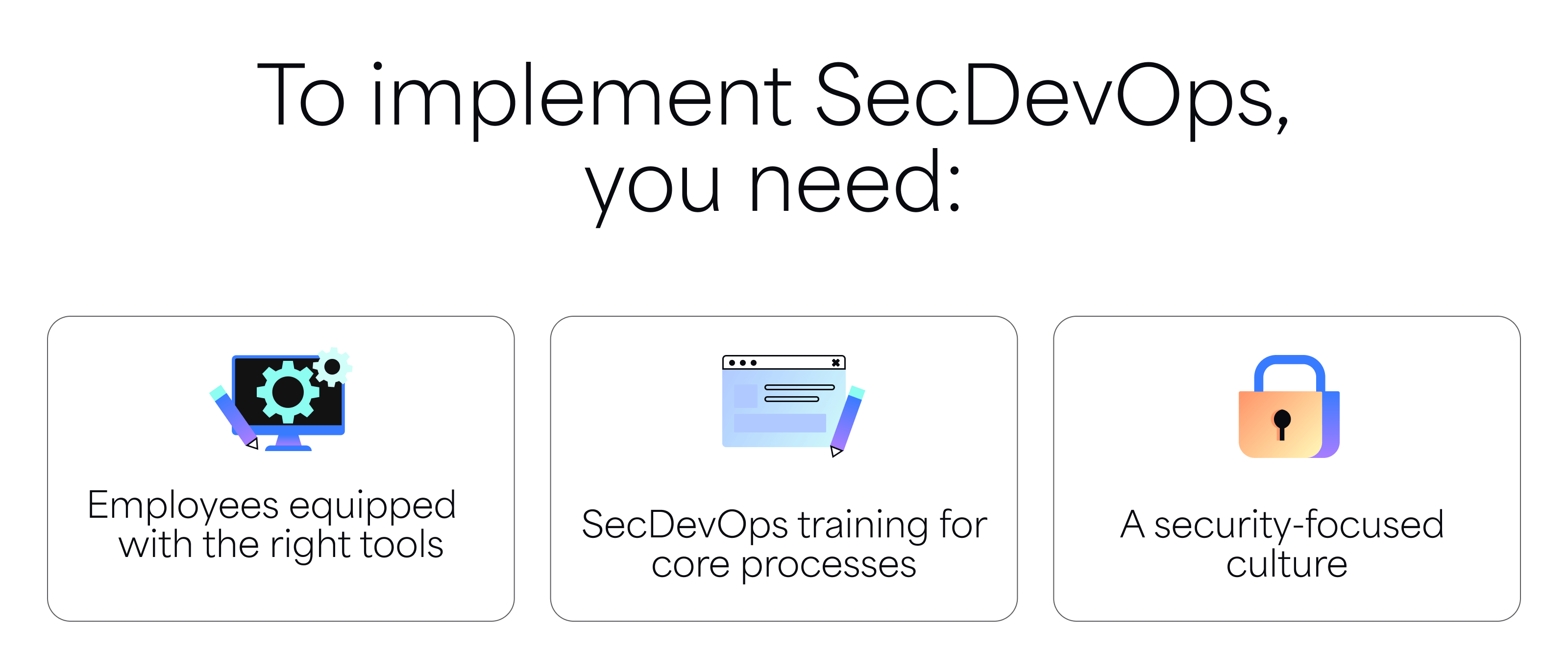
Here’s how to roll it out without stalling the team:
Start with what you’re already doing.
Got CI tests running? You’ve already got the loop. Add static analysis and vuln scans to that same pipeline. Keep feedback tight, fast, and where devs already live. If you’re using GitHub Actions, GitLab CI, or Jenkins, you’ve got what you need.
Use policy-as-code to enforce standards.
Ditch the checklist. Define your security rules as code and let your pipeline enforce them. Tools like Flow or OPA let you validate every PR without waiting on a manual review.
Automate the boring stuff.
Dependency scans, license checks, evidence logging, all of it can run without human hands. That’s fewer missed steps, and fewer Slack threads asking “did we check for XYZ?”.
Make security visible and fixable.
Don’t hide feedback in a dashboard nobody checks. Put it in the PR, in the IDE, in the CI output, right where work happens. If it’s easy to see, it’s easy to fix.
Iterate. Don’t try to secure everything on day one.
Pick your biggest risks, automate the checks, and expand over time. Security debt is real but you don’t have to pay it all at once.
The goal? A pipeline that ships secure code by default, not by exception.
Common challenges and how to solve them
Even with the best intentions, SecDevOps can trip up fast, especially if it feels bolted on. Here’s where teams get stuck, and what actually works.
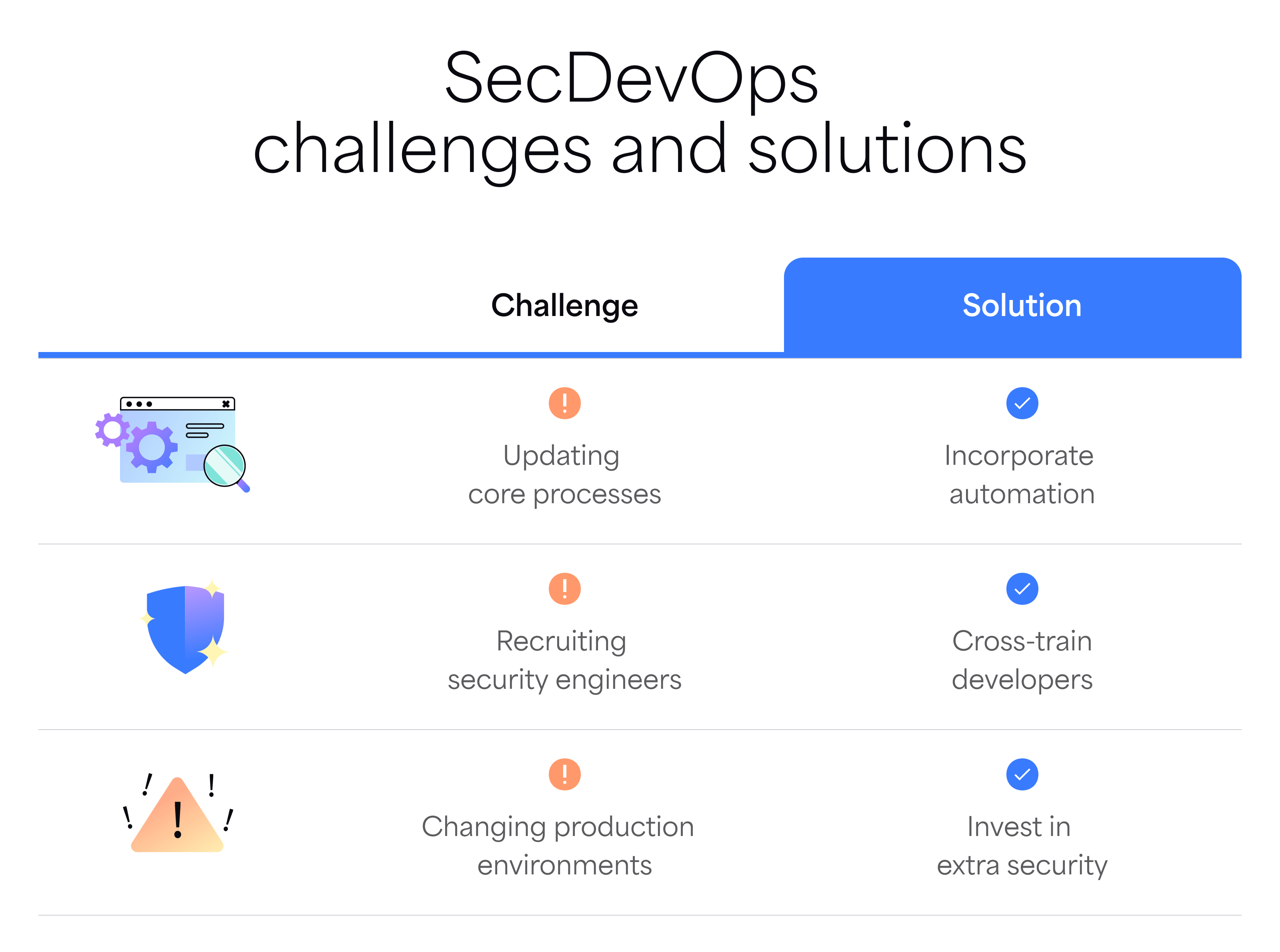
Developer pushback
If security creates noise or slows down PRs, trust erodes fast.
Fix it: Prioritize high-signal, low-noise checks. Keep them in the PR, not in a separate system. Start small. Don’t add a 5-minute scan to every merge and expect applause.
Tooling overload
Another dashboard? Another YAML dialect? No thanks.
Fix it: Choose tools that fit your stack. Git-native, YAML-friendly, zero new logins. Seamless beats shiny.
Compliance complexity
Dev teams aren’t signing up to manage the GRC binder.
Fix it: Automate evidence collection through your pipeline. Every merged PR, passed scan, or policy check leaves a trail. Compliance isn’t dev work, it’s a pipeline byproduct.
Fear of false positives
If everything’s critical, nothing is.
Fix it: Tune hard. Label clearly. Triage fast. Security signals should work like observability: fast, focused, and fixable.
“Too much to fix” paralysis
A mountain of vulns can stall progress before you even start.
Fix it: Don’t try to secure the whole repo at once. Secure what’s shipping next. Automate around your riskiest paths, then expand.
SecDevOps isn’t magic. But done right, it earns dev trust and keeps shipping unblocked.
A faster, safer pipeline starts with the right approach
If you’re already automating tests and deploying with confidence, SecDevOps is the next step, making security part of the same trusted flow.
No team overhaul. No new process. Just security as code, running where the code lives.
The best SecDevOps setups don’t slow teams down. They give developers confidence, reduce review bottlenecks, and keep risky code from slipping through the cracks.
Enforce policies automatically. Surface issues in real time. Track compliance in the background. Tools like Flow help make that happen, without slowing you down.
Because secure code shouldn’t be a blocker. It should be the baseline.
Ready to bake security into your pipeline, without breaking your sprint?
Try Flow